This lab covers IPv6 static and static default routes. Static routes are a manual way of defining the path a packet should take in the network to get to its destination. The command to write an IPv6 static route is similar to an IPv4 static route except you use the command IPv6 route instead of […]
This lab covers IPv4 static and static default routes. Static routes are a manual way of defining the path a packet should take in the network to get to its destination. The command to write a static route is ip route destination prefix destination prefix mask [outgoing interface | next hop IP address]. In regular […]
This lab only focuses on DHCP, you will need to begin with connectivity, which a good review as well. Before configuring the DHCP steps configure the topology to get connectivity throughout. You should be able to ping from the G0/0/1 interface on Branch to all other interfaces, you will not be able to ping from […]
Devices Used – 2 Cisco routers with 2 ethernet interfaces, 1 layer 2 switch, and a PC **You could use Packet Tracer instead of real devices for this lab. In this lab you will complete initial configurations hostnames, passwords, and IP addressing. Then configure OSPF with options and DHCP server on the HQ router to […]
Multiprotocol Border Gateway Protocol (MP-BGP) is an extension of Border Gateway Protocol (BGP) that enables the exchange of routing information for multiple protocols. MP-BGP is used in large-scale networks where multiple protocols, such as IPv4, IPv6, and multicast, are used, and it provides a scalable solution for exchanging routing information across different protocols. Benefits of […]
Virtual machines (VMs) and containers are both technologies that can be used to host applications in an isolated environment. However, they differ in how they achieve isolation and the level of abstraction they provide. Virtual machines are a type of software that emulates a physical computer, creating a separate and self-contained operating system (OS) environment […]
Social engineering attacks are a type of network attack that relies on manipulating people rather than exploiting technical vulnerabilities. These attacks can be difficult to detect and prevent because they rely on tricking individuals into divulging sensitive information or performing actions that compromise security. Some common types of social engineering attacks include: It is important […]
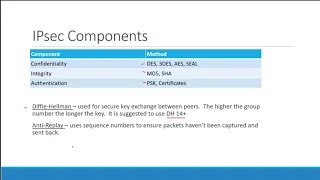
Network attacks are malicious efforts to disrupt, intercept, or gain unauthorized access to computer networks or devices connected to those networks. These attacks can compromise the confidentiality, integrity, and availability of network resources, and can be used to steal sensitive data, disrupt operations, or gain unauthorized access to systems. Here are some common types of […]